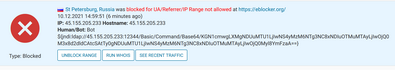
The log4j security issue that is discussed heavily in the media is not affecting eBlocker.
Actually, we were aware of this attack vector two days before the official authority‘s warning. We recorded and analyzed the attack pattern in a forensic log last Friday already:
Even eBlockerOS uses log4j, our particular implementation is not affected. Nevertheless, we will update the log4j component with the next maintenance release to stay up-to-date with current enhancements.
The eBlocker web servers as well as other centrally provided infrastructure (update servers, DynDNS, team collaboration etc.) is also not affected as we analyzed log4j is not used by these services.
[Off topic] I had the pleasure to talk about the log4j attack vector in the German TV "ZDF heute" news on Monday: https://www.zdf.de/nachrichten/heute-19-uhr/software-sicherheitsluecke-cybersicherheit-video-100.html [/Off topic]
Great news