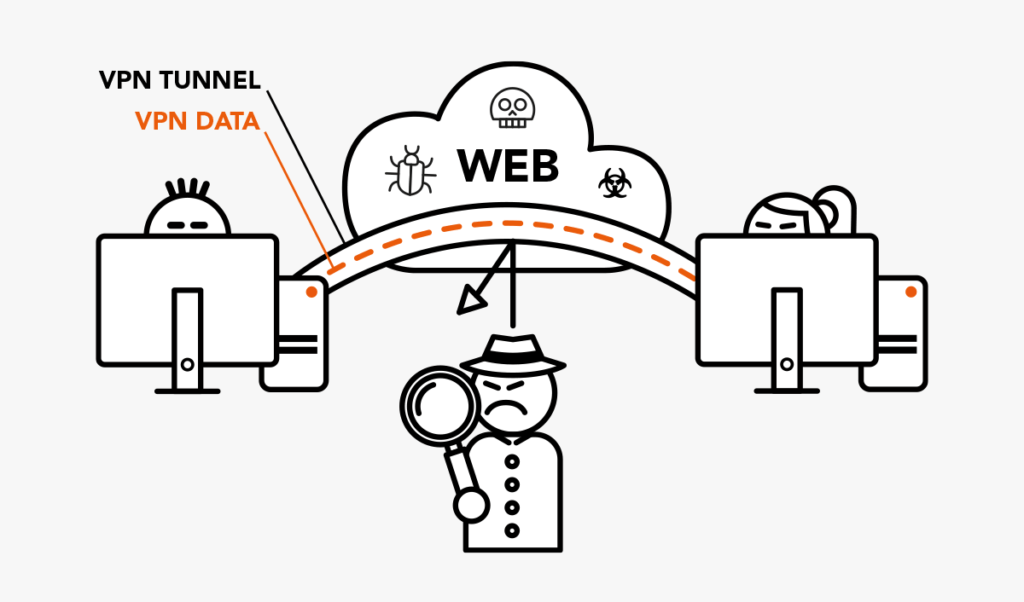
Anyone surfing the Internet is never unobserved. The data you exchange online with others is always visible to third parties. In theory, every e-mail can be read at every node on the Internet that lies between you and the recipient.
In order to prevent such snooping, there are various encryption and anonymization procedures. One of them is the Tor network. Another option is virtual private networks (VPN).
What is a VPN and how does it work?
A VPN works like an additional security shield that covers the existing connection. It builds upon your existing Internet connection, for third parties a further invisible and additionally still encrypted network – you surf then so to speak with Private Network!
To set up a VPN, a log-in server is required. You log on to this server via the Internet or your company network. Depending on the default settings, you may need a password or a previously received digital certificate, i. e. an individual numerical code that functions like a virtual ID card. There are also VPNs that are protected by hardware, such as a combination of password and personal handheld code generator.
Your end device connects to the VPN provider through a data tunnel (“tunneling”), the VPN provider then surfs the Internet practically on your behalf. For third parties, such as a website visited by you, your IP address is not visible, but only that of the VPN provider.
Most VPNs are commercial services that require a fee. As a rule, providers operate data centers with high bandwidth for this purpose, in order to channel all their customers’ data traffic via the VPN. If correctly configured, all your data packets will be routed over the VPN. Your Internet provider cannot see that you are on the move in a VPN and what you are doing on the network.
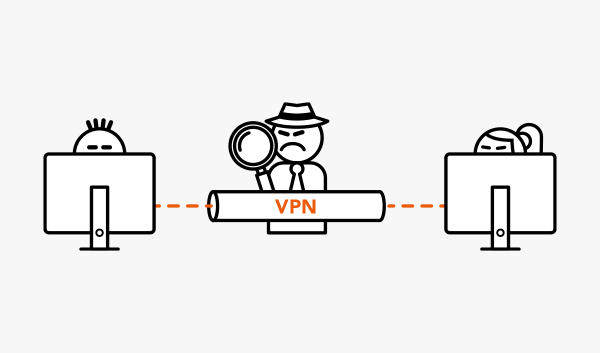
Key strengths and weaknesses of VPN technology
Advantages of VPN technology:
- High guaranteed bandwidths
- As a user, you can determine which country identifier your IP has and thus avoid geoblocking, for example.
- Your IP address is no longer visible to third parties because you are traveling with your VPN provider’s IP address.
Disadvantages of VPN technology:
- Usually for a fee
- Your data traffic runs through the data center of the VPN provider. At the end of the VPN tunnel, however, the data is decrypted again, so that the VPN provider can view your data packets.
- You must trust that your VPN provider does not record any data from you and does not store your real IP address.
- Many VPN providers have their headquarters abroad, where other consumer protection laws apply, and governments can read along, for example in China.
- Hackers and secret services repeatedly try to penetrate the server infrastructure of VPN providers because they are hoping for sensitive user data.
Tor vs. VPN
Just like in the Tor network, the data traffic between your end device and the VPN provider is encrypted. In contrast to Tor, the VPN only has one node on the way. Anyone who wants to exploit the advantages of both technologies will use Tor and VPN at the same time.
eBlocker, therefore, relies on the connection of Tor and VPN. You can choose whether you want to set up full protection for all end devices or whether you want to protect only those devices on which sensitive data is stored or with which you want to surf anonymously. With the eBlocker the choice is yours, take a look at all the features available in our solution.
Important note
Please note that this article was originally published by the former eBlocker GmbH. The contents may be outdated. Today, eBlocker is free of charge and available as Open Source. Check out the new eBlocker Open Source Project.