Hello,
I'm new to this forum and also to eBlocker.
I installed eBlocker in a Raspberry Pi 4 and everything look ok.
But when I enabled HTTPS my Telegram APP stuck at CONNECTING... and don't work.
I already imported the SSL Certificate using keychain and also checked TELEGRAM at Trusted APPs.
Nothing suspicious is showing at COMMUNICATION FAILURES.
Can you help me?
Thanks in advance.
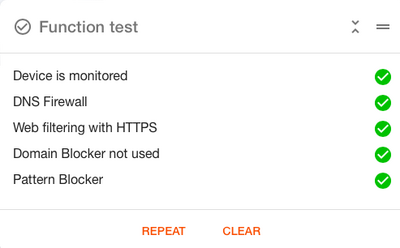
@dxisto Firstly, please make sure that the Function Test in the Dashboard shows only green check marks, when eBlocker HTTPS is enabled. The Dashboard is device individual, so run the Dashboard on the same device you installed the certificate in.
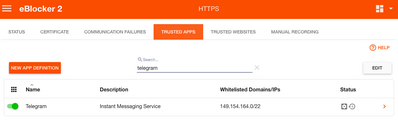
Secondly, make sure the Telegram Trusted App is enabled (Settings>HTTPS>Trusted App)
In case Telegram does not work still, please follow https://eblocker.org/en/docs/manual-recording/. If you need help adding the right domains, please share outcome of the recording here (using screenshots).
THX!
@dxisto Firstly, please make sure that the Function Test in the Dashboard shows only green check marks, when eBlocker HTTPS is enabled. The Dashboard is device individual, so run the Dashboard on the same device you installed the certificate in.
Hello @random, thank you for your reply.
Yes, Function Test shows only green check marks:
Secondly, make sure the Telegram Trusted App is enabled (Settings>HTTPS>Trusted App)
Yes, Telegram is enabled as Trusted App:
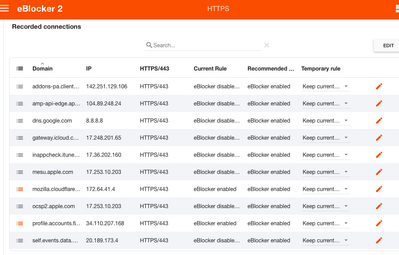
In case Telegram does not work still, please follow https://eblocker.org/en/docs/manual-recording/. If you need help adding the right domains, please share outcome of the recording here (using screenshots).
Telegram app still not working:
And sadly Manual recording doesn't shows anything promissing:
@dxisto Thanks for the screenshots. Unfortunately I'm not a Telegram user, so I am guessing:
I tried to look for sources where the Telegram IP addresses (used for communication) are listed and found this: https://docs.pyrogram.org/faq/what-are-the-ip-addresses-of-telegram-data-centers
What you can try is to add those IPs (just the IPv4!) to the Telegram Trusted App. Just hit "Edit" in the Trusted App and add each IP in a separate line.
In case this does still not work, you can try to trust not just the single IPs but the full (class C) network by changing the last digit to ".0/24". So change 149.154.167.51 to 149.154.167.0/24, for instance. BTW: Chances are low you are trusting a "malicious" tracking IP by chance, so no worries about trusting the class C networks.
Hope this helps.👍
Would be great if you could report back if you succeeded.
THX!
Based on your tip @random I found this:
https://core [DOT] telegram [DOT] org/resources/cidr.txt
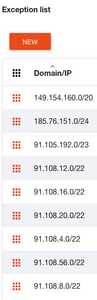
After I added all IPv4 blocks in the Telegram App exception list (which originally only had 149.154.160.0/20 block), it worked like a charm!
Now Telegram App exception list looks like this:
But that raises another question: Why this communication issue was not shown at COMMUNICATION FAILURES neither in MANUAL RECORDING?
Thank you very much for your support!
@dxisto Good find! Thanks a lot. 👍
Would you be so kind and paste the URL again with "domain dot com" as the forum strips links for new users (sorry😢).
Alternatively you might want to share the IP ranges as text to copy/paste for other users. We will update the pre-defined Trusted App asap as well.
But that raises another question: Why this communication issue was not shown at COMMUNICATION FAILURES neither in MANUAL RECORDING?
I'm not a developer. To my knowledge eBlocker monitors SSL errors while recording the app communication. Not all communication yields to errors. So I assume the given IPs throw no SSL errors, but rather detect eBlocker's interference somehow and block communication. But this is just a guess.
THX!
@dxisto Good find! Thanks a lot. 👍
Would you be so kind and paste the URL again with "domain dot com" as the forum strips links for new users (sorry😢).
Alternatively you might want to share the IP ranges as text to copy/paste for other users. We will update the pre-defined Trusted App asap as well.
Sure! I’ve edited my previously post and I think it’s intelligible now.
But for copy/paste sake, these are the IPv4 CIDRs:
91.108.56.0/22 91.108.4.0/22 91.108.8.0/22 91.108.16.0/22 91.108.12.0/22 149.154.160.0/20 91.105.192.0/23 91.108.20.0/22 185.76.151.0/24
I'm not a developer. To my knowledge eBlocker monitors SSL errors while recording the app communication. Not all communication yields to errors. So I assume the given IPs throw no SSL errors, but rather detect eBlocker's interference somehow and block communication. But this is just a guess.
THX!
In order to try to help developers, the squid error produced was something like:
<timestamp> 79102 <ip> NONE_ABORTED/000 0 CONNECT 149.154.175.53:443 - HIER_NONE/- -