eBlockerOS 3 has been released today (Dec. 20, 2023). 🚀
This thread is to collect all issues regarding IPv6. If your issue is not related to IPv6, please open a new thread instead.
Please make sure to read the know issues and restrictions (also available in German) of the IPv6 implementation before posting here.
THX!
I updated my system today but I am struggeling with many issues.
I noticed the following:
1. you need to check and un-check the IPv6
2 you need to re-install the certifcates
3. also after reinstalling the certifcates the eblocker is not working properly
I had too much time to investigate in the issues but right now it is not working on all my devices (Windos, and iOs).
I can confirm that all other parameters and definitions are fine since I know the eblocker for many years.
Any ideas what is going on?
@nik Thanks for your feedback. I have a couple of questions:
Did you update an old eBlockerOS that wasn't used for a while or did you update an eBlocker that was working well (with eBlockerOS 2.10.x) and used it for protection your network all times?
In case eBlocker was running all time, have you disabled IPv4 on your router?
1. you need to check and un-check the IPv6
2. you need to re-install the certifcates
How do you come to these conclusions?
- What was not working and what changed after re-enabling the switch?
- Why do you feel you needed to install the certificate anew? What error did you get?
Please email us the certificate from your eBlocker to support at eBlocker dot org. (Just download the certificate using Settings> HTTPS> Certificate Tab and hit the download button.)
Also it would be great if you could export the old certificate from your browser and send this as well.
THX!
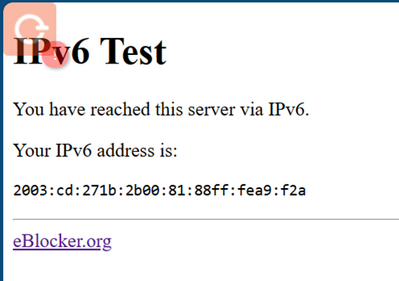
@nik Could you please also take a screenshot of the screen you are getting when visiting the following link: ipv6.eblocker.org
THX!
1. yes - I updated the eBlocker OS. The last update was 3 days ago.
I am observing the eBlocker probably 10 times a day 😉
...did several rules for Samsung TV etc.
2. after check and un-check the IPv6 I got some webpages - but not all webpages
> I have no access to most (only most - not all) webpages.
3. you need to re-install the certifcates -> see #2
4. upload new certificate
best
nik
@nik Please email the certificate as stated above.
I wonder how eBlocker ever worked in the past if you are using IPv6. 🤔
Did you just enable IPv6 on your router/client purposely or was there no change?
Nevertheless, to me it seems the certificate was never installed correctly and the "stern" issue is not related to the update at all. Please open a new thread if the issue persists (after rebooting the client) and provide the info asked here: https://eblocker.org/community/announcements/before-posting-here-please-read/#post-117
Otherwise this thread gets busted with non eOS3 related posts and we loose focus.😉
THX!
Update: however I needed to reinstall on the Windows machine again the certifcate.
I don't know why, but it was previously confirmed as installed but it wasn't.
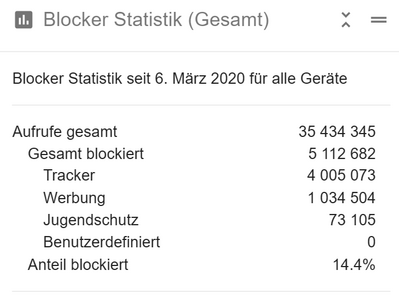
This is my statistic from the last years.
Now the miracle 2.
After 1h of testing it works fine on iOS too. Can't figure it out why.
I will update in case there is still something strange going on.
Due to the reason that I was one of the first users I can tell you that the Banana Pi is pretty slow. Need to update finaly.
@nik Just for clarification here is what happened from my perspective:
Under eBlockerOS 2, you
- did not disable IPv6 as documented
- did not install the certificate properly on the macOS/iOS clients (probably missing to grant CA/root trust)
Now what happens under these circumstance under eBlockerOS 2:
- macOS (and probably iOS, too) always resolves domain names via IPv4 UDP (not using IPv6)
- eBlockerOS 2 DNS resolves this IPv4 request - and blocks the bad domains
- So you partly get protection on domain level and saw less ads etc.
- BUT all data traffic (=non DNS) is send by macOS/iOS via IPv6, resulting in by-passing eBlockerOS 2 completely. Hence, eBlocker's advanced pattern matching blocker never got used.
With the update to eBlockerOS 3
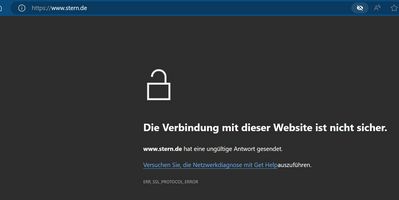
- Now all IPv6 data traffic is analyzed by eBlocker, but this fails as the certificate was not granted trust. Resulting in the "stern" error message above.
- Once you correctly installed the certificate, the eBlocker icon appeared and everything works as expected.
In conclusion: you had mal-configured clients and a network using IPv6 with eBlockerOS 2, which you didn't notice until the update. So the issue was just a human error!
Nevertheless, the eBlockerOS 3 update worked as expected and there is no technical problem (in this case), which you confirmed above.
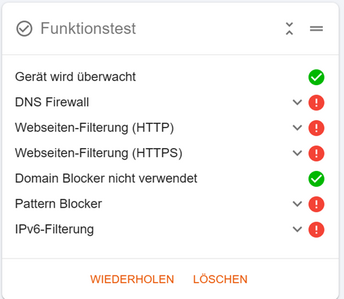
Last hint: Perform the Dashboard Function Test on every(!) single device as the test is device dependent. This will show if you missed to install the certificate correctly on a device, which is mandatory for the advanced pattern matching blocker to work.
In case this was all to technical and complex, my very personal advice: It's a usually a good idea to follow the documentation closely. As @benne always says: as soon as you do it right, it just works 😉
THX!
From the Discord channel we got the info that the backup is not working, since eB v3.
I can reproduce this export behaviour on a new install, doesn't matter if with https and password or without. On my Prod eBlocker this is also no more possible.
http error 500
The returned app min js file is empty.. or took too long to load...
Also there is again a problem with the eBlocker internal dhcp service, when using "Expert mode" with EXTERNAL dhcp...
Even if this is correct, the devices show in the ipconfig that the eblocker ip is serving dhcp..
To stop this misbehaviour, the command "systemctl disable isc-dhcp-server" on the console helps.
regards
@calimero Thanks for the feedback. I can confirm the backup issue.
Also there is again a problem with the eBlocker internal dhcp service, when using "Expert mode" with EXTERNAL dhcp...
Is this happening on a VM install? If I remember right, we had a similar issue a while ago, which affected VMs only.
THX!
Thanks for update but I can confirm that the "Funktionstest" were fine in the past. Because of my paranoia I am checking that pretty frequently.
I also needed to clean up my DNS cache to let it work. There were again some issues with some webpages this morning although it worked fine at midnight.
So let me do further test and I will report.
BTW the backup does not work. I was thinking of upgrading my system to PI4.
Thanks in advance
Nik
Hello everyone, first of all many thanks to the E-Blocker team for their great work.
Now I have a problem with the IPV6 support. My cloud is accessible from the Internet via V6. As soon as I activate V6 support, I can no longer connect to the cloud from outside.
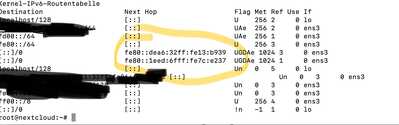
If I deactivate the support everything is ok. I have noticed that the blocker announces its local link address together with the address of the Fritzbox. Two routers are then apparently reported on the Raspbian. See screenshot. I'll try to deactivate IP V6 DHCP and only enter the Fritzbox. Is this behaviour normal?
Best regards
Translated with DeepL.com (free version)
@nik Actually you are only able to build up the Pi4 in parallel and open BOTH webpages side by side to copy and paste your settings...
What you also need to deploy on all devices is the https certificate again, as this will be a complete new one..
Regards
Thanks for update but I can confirm that the "Funktionstest" were fine in the past.
Well, then some "magic" must have happened since. Some of the magic must have activated IPv6 in your network, for instance. Unfortunately you didn't answer my question above whether/when you've enabled IPv6. I fear you might have also missed the warning note in the Release Notes and the Blog Post regarding the activation of IPv6 in the network. 🤔
Nevertheless, it's a fact that if IPv6 is active in the network, Function Test will fail under eBlockerOS 2. And it's another fact, that certificates where not touched with eBlockerOS 3 and therefore would hardly cause the error you've encountered. The error you mentioned is very typical for a wrong certificate installation if docu is not followed closely, btw.
But maybe day comes when we find out about the magic happening in your network.😉
BTW the backup does not work. I was thinking of upgrading my system to PI4.
It's a known issue (see this thread) and will be fixed early next year. Patience is key 👍
THX!
@rene A couple of questions to understand your configuration better:
- You run a nextcloud server in your local network, right?
- How do you mange to make this server accessible from the Internet ? (Detailed explanation please)
- Do you run HTTPS on the server (ie. do you have a valid SSL certificate)?
- How do you access the nextcloud? Web interface via HTTP or HTTPS or some other protocol?
- Is eBlocker set to protect the nextcloud server (ie. is the server enabled under Settings> Devices)?
Two remarks:
- The eBlocker is acting as an IPv6 router with high priority. So seeing two routers is normal therefore (ie. your original Internet router and eBlocker).
- IPv6 does not need DHCP, so I'd rather refrain from running an IPv6 DHCP as this might cause unnecessary side effects. eBlockerOS 3 expects no IPv6 DHCP in the network (at the very moment).
THX!
@calimero Thank you for the info, I can confirm that the backup is broken in 3.0.1. I have written an issue and I am working on it: https://github.com/eblocker/eblocker/issues/321
@Random thanks for the quick reply.
1. yes running local
2. only ip V6 activated. Then in the Fritzbox port 443 redirected to the V6 IP. Without blocker everything works.
3. yes Https with official ssl certificate. So that the cloud is also accessible from the company.
4. only https. Everything else is deactivated.
5. no the e-blocker is deactivated for the cloud.
You are right that it does not need a local DHCP. It has something to do with the blocker as a router. Wouldn't it be done if the blocker passed everything directly to the standard router when set to "OFF"?
Translated with DeepL.com (free version)
Hello everyone,
Here is my solution for the moment. In the /etc/network/interfaces
set the IPV6 address and the gateway fix. For example :
iface ens3 inet6 static
address XXX:CCCC:RRRR:TTTT:22:4444:6666:7777
gateway 1111::2222:3333:4444:5555.
This is how it works for me. The Raspbian ignores the E-blocker. This is how I get a connection from outside again.
Maybe it helps one or the other.
Greetings
One more question: .... only V4 servers are accepted as external DNS servers. Does this make the DNS firewall ineffective?
only V4 servers are accepted as external DNS servers. Does this make the DNS firewall ineffective?
eBlocker's DNS server accepts IPv6 but unfortunately the user interface is not. This is a minor glitch we can probably fix quickly. Thanks very much for finding it 👍
To my knowledge DNS is transparent, so despite the absence of an IPv6 DNS entry the firewall works effectively due to dual stack handling of the OS. macOS for instance always uses IPv4 to resolve DNS even if IPv6 is available...
So I wouldn't worry too much about the glitch for the time being. 😉
THX!
You are right, only IPv4 addresses can be set as external DNS servers currently. But this is not a problem for IPv6 because:
- eBlocker's DNS can still be reached via IPv4 and IPv6 from clients in the home network
- eBlocker's DNS can still resolve IPv4 (A) and IPv6 (AAAA) addresses
It's a bit confusing, but these things are totally independent:
- Whether the client uses IPv4 or IPv6 to talk to eBlocker's DNS server
- Whether the client requests an IPv4 (A) or IPv6 (AAAA) address
- Whether eBlocker's DNS uses IPv4 or IPv6 to talk to external DNS servers.
All combinations of the above are possible. (With the exception of external IPv6 DNS servers, currently.)
So as long as eBlocker has an IPv4 connection to the internet and external DNS servers have IPv4 addresses, everything should be fine.
I have added a TO DO: https://github.com/eblocker/eblocker/issues/322
@calimero To my knowledge the "backup save issue" is already fixed. But it has not been tested yet and therefore it will not be released untested. As with eBlockerOS 3 you are highly invited to test the new version and let it pass more quickly to release...
In addition please also consider that not all parameters are saved in a backup. If I remember right, Network and DNS setting are not ending up in the backup at all. This is intended and not a bug.
So rather than "disabling the backup" I'd suggest to just verify everything is set as expected after restoring settings from backup. Easy 👍
THX!
@random Thanks for your reply... I can't use backup in the testimage for the IPv6 tests... which image/stage is it available?
DNS log threw errors after restoring (/opt/eblocker-dns/log), but I will check that again with the user
@bpr is there an info, which settings files would be needed to catch, so we had almost all data for restoring?
Best regards and a happy new year
Happy new year, @calimero and @random!
The backup feature is fixed but only in GitHub. I will have a new update in the test/dev environment later this week.
Regarding the DNS problems: the configuration is written dynamically by the Java component and sent via Redis to eblocker-dns. So there are no settings files.
If the user could create a diagnostics report and send it to "support AT eblocker.org" I can take a look at it. Maybe there is some inconsistency in the Redis database.
Hello everyone, I've been an Eblocker user from the very beginning. For your information, I have always deactivated https support because I always had problems with various websites.
Now to my problem with IPv6. My internet connection is a full IPv6 connection (no tunnel to IPv4).
After the eblocker was updated to version 3.0, my internet speed (1000/50) was suddenly only a third (200-300Mbit).
I then thought it was the provider's fault, they checked everything but couldn't find anything wrong.
Now, after much trial and error, I have found out that as soon as I deactivate the IPv6 filtering in the eblocker, I get the full 1000 Mbit again. Of course, the IPv6 line is now not "protected". As soon as I reactivate IPv6 filtering, the speed drops back to 200-300 Mbit. Do I have to set anything else in the Fritzbox 6660 with regard to IPv6? With IPv4 I have DHCP off and everything runs via the eblocker. I have also deactivated DHCP6 for IPv6. Do I have to store the IPv6 addresses (local & global) of the eBlocker in the Fritzbox? I can't get any further. Thank you for your support.
I guess the explanation is probably simple...
I have always deactivated https support
To my knowledge, in this case only DNS requests (resolving domain names) are passed to eBlocker but all other IPv4(!) traffic is by-passing eBlocker's network interface (going straight to the router).
Now with IPv6 eBlockerOS announces itself as the gateway/router. Then (technically mandatory) all IPv6 packets are run thru eBlocker's network interface. As the interface is 1000 Mbit/s (for White Cube & Raspi 4) you will in theory never ever get more than 500 Mbits thru-put because in- and out-bound traffic is routed thru the same interface (= one Ethernet port).
In addition TCP/IP has a few percent overhead for header and other routing info, hence net you will only get less than the 500 Mbit/s. Probably like 400-450 Mbit only (in theory) on a 1000 Mbit/s interface.
Furthermore passing all packets back and forth needs some computation on eBlocker as well, so the real bandwidth will be less again. 300 Mbit/s although sounds too less, but that depends on the eBlocker hardware and it is realistic for the White Cube (an 8 years old hardware!) I'd guess.
To sum up: everything runs as expected and it's not a bug but the bandwidth is limited by your eBlockerOS hardware only.
So unless you run eBlockerOS on a hardware with a 2500 Mbit/s (or higher) network interface you will never get 1000 Mbit/s thru-put. Thus I'd recommend to move to a higher end hardware and run eBlockerOS VM-edition in case you really need 1000 Mbit/s.
But honestly from my perspective: there is no difference at all in terms of Internet browsing speed beyond 200 Mbit/s as HTML rendering speed in the browser is the limiting factor then. More that 200 Mbit/s Internet speed only shows an advantage for very huge downloads, where you could always pause eBlocker to get full speed.
THX!
@rigo I thought about your setup again. You can try to get the same effect with IPv6 as with IPv4 (just DNS via eBlockerOS) as follows:
Note down the first of eBlocker's IPv6 addresses you see under Network> IPv6. Then disable IPv6 (announcement). The eBlocker will still keep it's IPv6 address!
Then add this IPv6 address as DNS server in your IPv6 client's network configuration. You might need to switch to a static network configuration for your client to do so.
Hope this helps.
THX!
To sum up this lengthy thread for new readers looking into eBlockerOS 3 here are the known issues and their status:
- Backups can not be saved with eBlockerOS 3 yet. The good news: old backups can still be restored as usual in eBlockerOS 3. The bug is fixed and will be released in 3.0.2 (or higher)
- In the very special case of routing IPv6 packets from the Internet to an internal IPv6 only server, the routing fails. This is true even if the internal server is disabled for eBlocker protection. To work-around this issue set the router as static gateway in the IPv6 internal server. This issue will be fixed somewhen in future (as it needs more time for investigation and the case is not affecting the general users).
- With very high Internet bandwidth (above 1000 Mbit/s) IPv6 packets are routed via eBlocker's network interface even if just the Domain Blocker (=no eBlocker HTTPS enabled) is used. This can result in decreased bandwidth (of ~300 Mbits/s). There is a possible work-around sketched out above. Nevertheless, for full protection of 1000 Mbit/s bandwidth an eBlockerOS hardware with a 2500 Mbit/s port (or higher) is needed as the limitation is the network interface speed.
- Not related to eBlockerOS 3 in particular but still a new issue: tls-crypt is not yet supported with VPN providers. A fix will be released with 3.0.2 (or higher).
We'll be coming up with eBlockerOS 3.0.2 (or higher) during January 24 which fixes the backup and tls-crypt issues (and brings minor internal improvements).
In brief: eBlockerOS 3.0.1 runs very well in 99.9999% of the cases. The update is highly recommended to all eBlockerOS users. Big thanks to the team for this great release!👍
I'm closing this thread here. Please feel free to add new threads even if the issue is happening on eBlockerOS 3. Please make sure then to check this forum as the issue is probably not related to eBlockerOS 3 in particular.
THX!
eBlockerOS 3.0.2 has been released yesterday. It fixes the TLS crypt support among other minor issues.
THX!