Privacy Protection
Friends Protect Friends: Free License Key
In the reality helping friends and protecting them is just normal. To ensure this also happens on the Internet, we have launched the “Friends protect friends” campaign….
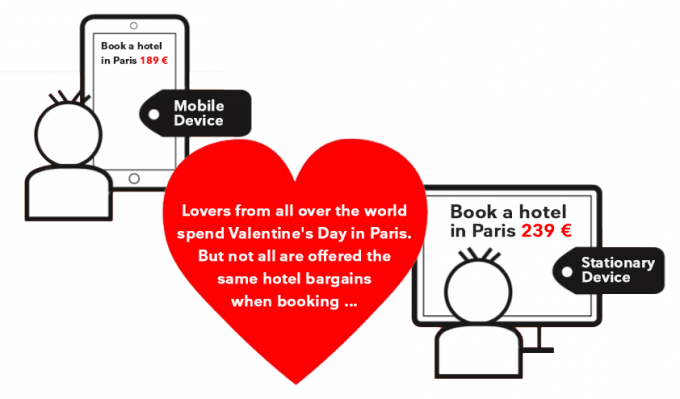
Visit the city of love for a cheap price on Valentine’s Day
How to save cash when booking a hotel on the Internet The same city, the same hotel, the same travel period – only the price is completely…
Browsing While in Incognito Isn’t Protecting as Much as You Might Expect.
Many are already familiar with the feature in most browsers to “hide” your browsing history. Chrome calls it “Incognito,” Edge named it “InPrivate” and Firefox calls it…
Without Online Protection You’re Maybe Throwing Away Money
You’re being watched, followed, and a profile is built about you as you leave traces of your visits while online. Even the German newspaper Springer wrote an…
Health Insurance Companies Are Spying on Customers
The penetration of US healthcare portals with web trackers like Facebook, Google, and various third-party trackers is more extensive than one would expect. Using an online tool…
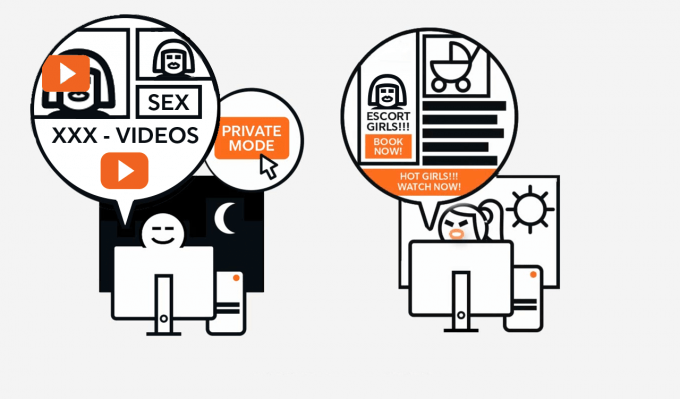
Adware: Advertising and Viruses Through The Back Door
If the browser suddenly leads to piquant Internet pages, the favored search engine falters or unknown programs appear on the computer, so-called adware is usually involved. But…
Phishing: When Criminals go Fishing by e-mail
More and more fraudsters try to lure unsuspecting Internet users to manipulated Internet sites with deceptively genuine phishing e-mails. Anyone who enters access data or passwords here…
Malvertising: Harmful advertising
Advertising on the Internet is not only annoying, slows down the page layout and increases the data volume: Sometimes banners and pop-ups even cause real dangers –…
Cybergangsters Now Tap The Computing Power Of Computers
Cybergangsters are usually keen on credit card data or passwords, now they have their sights set on a new target: stealing computing power, so-called cryptojacking. Hundreds of…
Tips to Prevent Internet Threats
In the digital age, clever thieves no longer steal handbags or crack cars: they are targeting the data and money of Internet users. The number of people…
Everything about viruses, malware and other pests
They are available in countless variations: few are just annoying, most of them are extremely dangerous. It is easy to catch them, but it’s difficult to get…
eBlocker Privacy Check
Run our Privacy Check page to learn what data your browser is sharing. You’ve probably read that when you are surfing the Internet, you are leaving traces….
10 Steps to Protecting Your Online Privacy
Restore your online privacy with these 10 steps! Unlike other media, such as radio, TV or print, on the Internet you are constantly leaving traces. Online trackers…
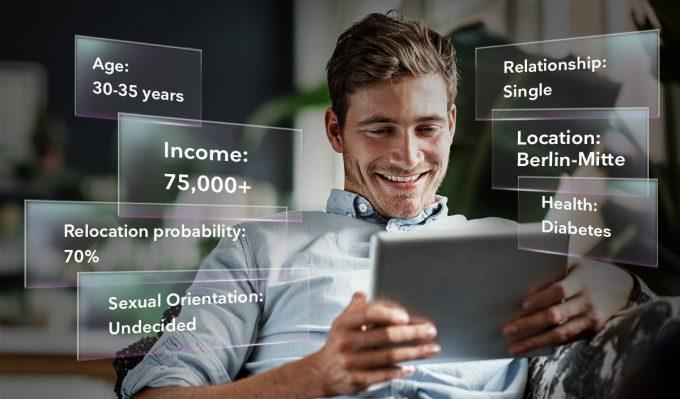
What does the Internet know about me?
Word has spread: Surfing the Internet leaves traces. How many clues are there, how expressive they are and how deep they penetrate our privacy – is surprising…
Tor-Network: Anonymous surfing according to the onion principle
Anyone surfing the Internet leaves behind traces of data that can be traced back to the user. Experts, therefore, recommend anonymizing tools that make traceability via the…
Setup a VPN: How it works
To set up a Virtual Private Network (VPN), you must first create a user account with a commercial VPN provider and specify how you want to pay…
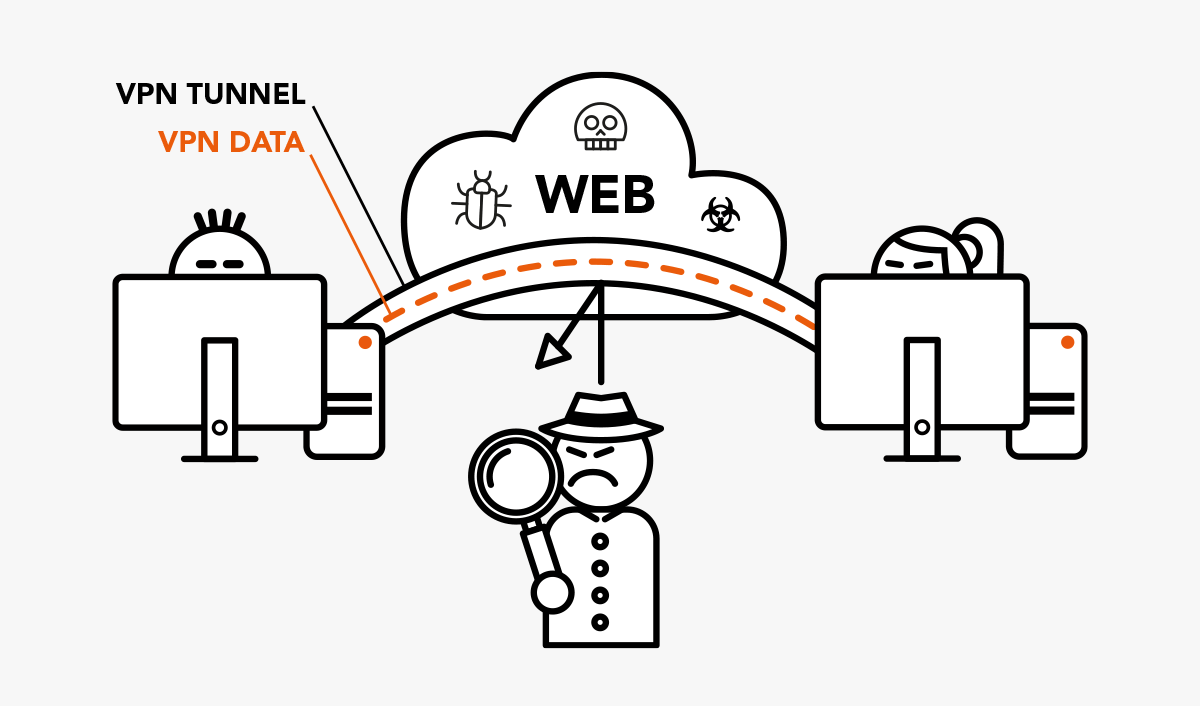
VPN: Surfing with a Private Network
Anyone surfing the Internet is never unobserved. The data you exchange online with others is always visible to third parties. In theory, every e-mail can be read…
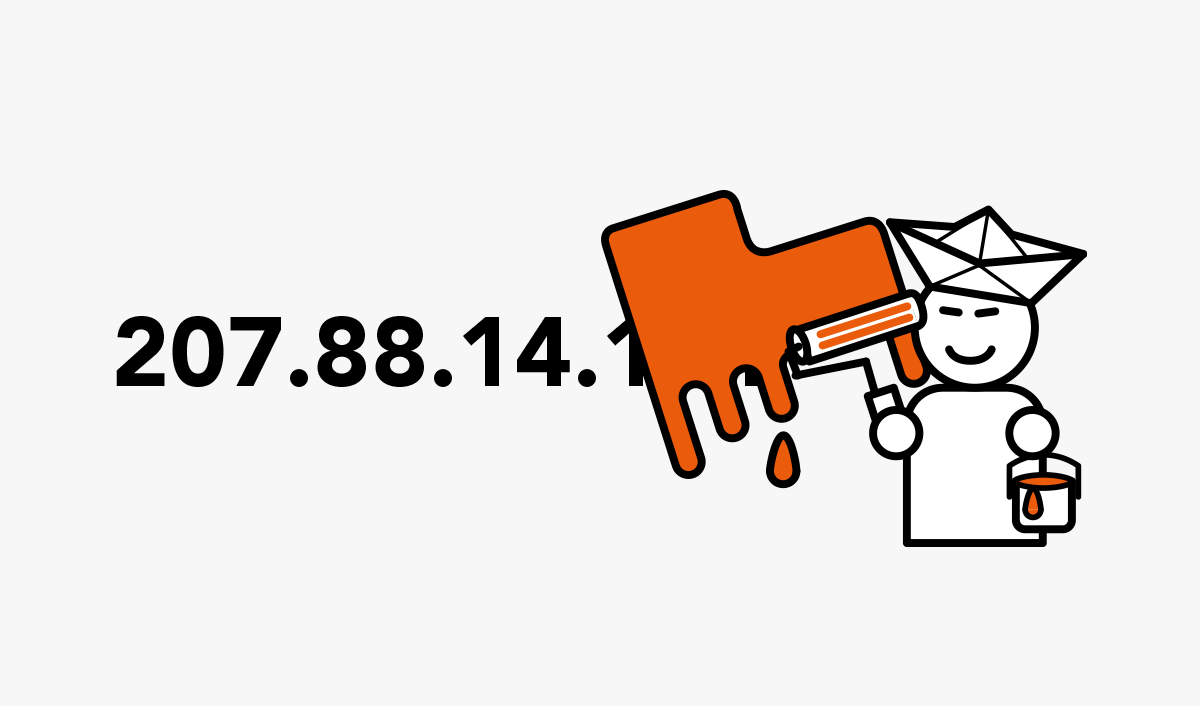
Why should I hide my IP address?
For unique identification, a device requires an address within a data network – be it in the home LAN or on the Internet. This is the only…
Big Trouble in Little Data
‘Big data.’ ‘Metadata.’ ‘Raw data.’ B.J. Mendelson has a passion for privacy, so he created a book “Privacy” from his collection of essays on privacy protection. This…
Why Should I Pay More? How to Avoid Dynamic Pricing
Who buys cookies in the supermarket, pays the same price as all other customers. But the Internet has its own laws: More and more retailers rely on…